Welcome to the
WalkMe Help Center
Please log in to continue

Please log in to continue

Easily access your upcoming meetings and join them from the desktop/mobile menu.
View and join upcoming meetings from the home screen widget.
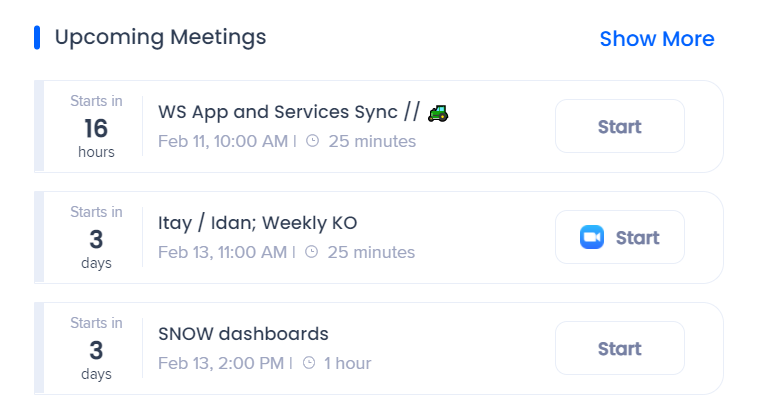
Additional to Zoom, other third-parties that are integrated with Outlook Calendar such as Webex and Gong are supported.
The Enterprise Search uses 3rd-party integrations to implement a "federal search". Searches within the menu are backed by an NLP engine, and a graph database that supports a great user experience.
The Enterprise Search doesn't index 3rd-party data on an independently searchable database.
See below sequence diagram describes the searching algorithm:

To activate the Enterprise Search (and the Personalized Workspace widgets), each employee is required to grant the menu permission to access the 3rd-party.
The granting process is using the OAuth2.0 protocol.
Each time a new access token is granted to the menu, the application will encrypt the access and refresh tokens and store it in a remote database.
The encryption process includes a unique private key ("salt") that is generated for each individual at the very first bootstrap and stored in the local machine Keychain.
The salt is irreplaceable and not restorable -- losing it causes the access tokens to be voided.
This security measure is being taken to eliminate identity spoofing when accessing high-sensitive data.
See Figure 1.1 to review the salt generation and storage flow.

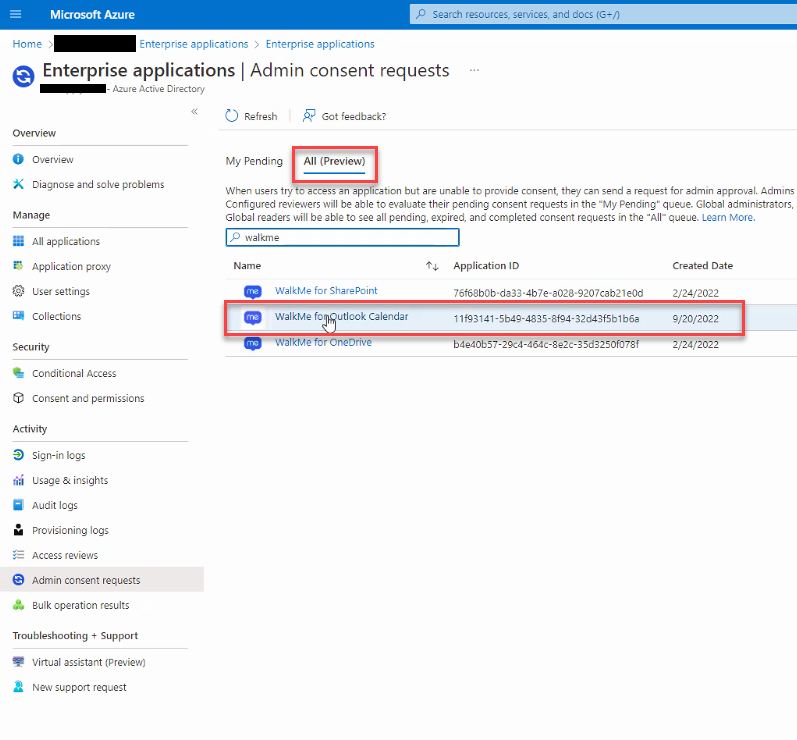
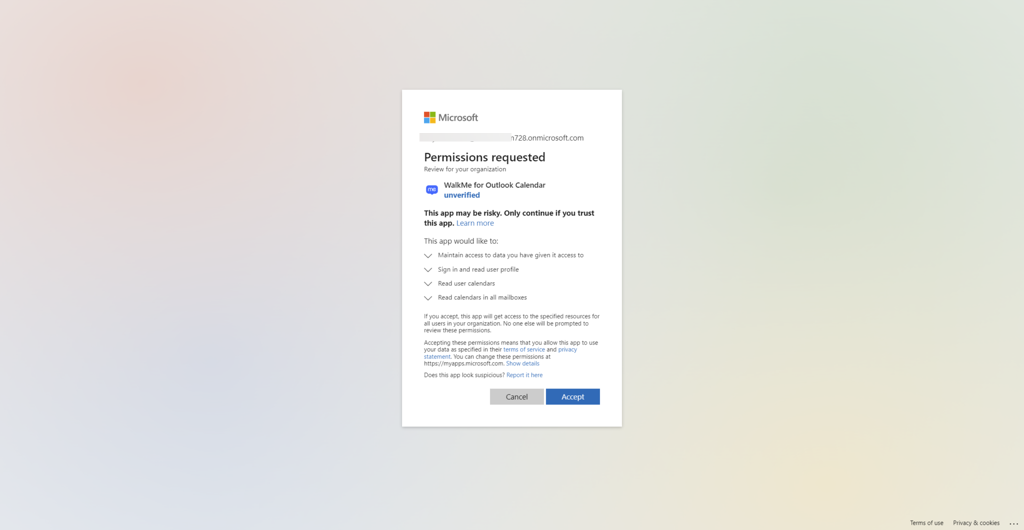
Accessing 3rd-party content requires end-user consent, and in some cases, mostly on Microsoft products, an organization admin consent.
End-users grant the menu the necessary permission by approving an OAuth2.0 consent screen that is being triggered by them from the menu application (“Third-party apps”).
The third-party apps are being approved and verified by third-parties products.
By the end of the granting process, the third-party apps provide access and refresh tokens that are used by the search engine to establish the requests.
See 3rd-Party Access and Refresh Tokens section above for more information about the storing mechanism.
While searching, the search engine forwards the request, before hitting the Adopter Service, through the Token Injector; a service that injects the relevant tokens to accomplish the request.
The local private key is being handed off over the search HTTPS request for runtime decryption.

When an end-user initiates a search query - the WalkMe enterprise search starts a search flow that is being protected by a JWT assigned by WalkMe IdP integration, as part of the end-user signing flow:

The JWT is proxying the user identity and keeping any HTTPS request secured and individual.
All desktop/mobile menu requests are protected by a JWT validation.


If the Outlook Calendar card is not available, contact your WalkMe Owner in your organization and ask to enable Outlook Calendar on the menu using the console.
Integrations can be segmented to a sub-set of users and audiences, rather than being enabled for all end-users. This feature streamlines the integration process and helps to ensure that users are only using the integrations that are relevant to their work.
To segment a menu integration: