Brief Overview
Identity Providers store and manage digital identities, providing a way for companies to manage access and privileges, while maintaining high security standards.
IDP Integration can be used to take that information, validate end-users identity, enrich content segmentation capabilities and expand on user behavior monitoring. Providing one reliable and secure User ID across any system without the need of defining the unique user ID for each system with different variables.
Using IDP as a User Identifier should be the go-to solution for all new systems.
IDP Integrations are accessible from the Admin Center at admin.walkme.com.
🎓 Digital Adoption Institute
Use Cases
- Make IDP authentication a prerequisite to present WalkMe content
- Expand content segmentation capabilities by IDP parameters, such as region or department
- Ensure accurate data monitoring across systems
Adding an Identity Provider
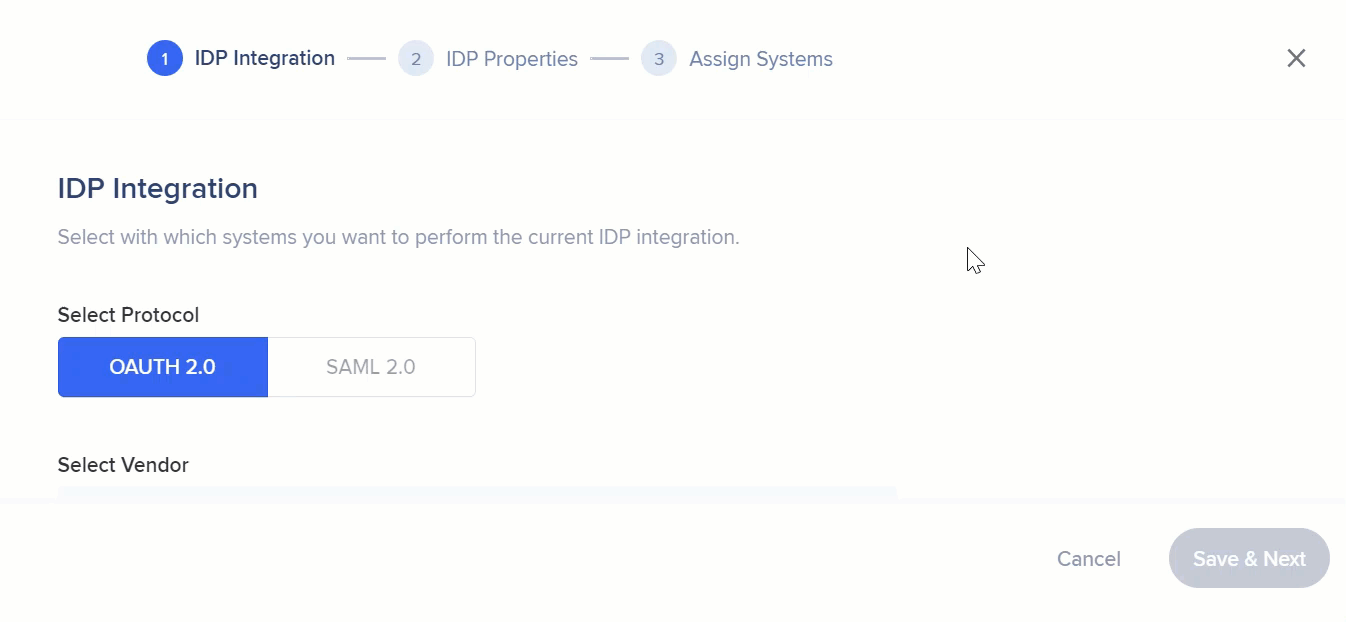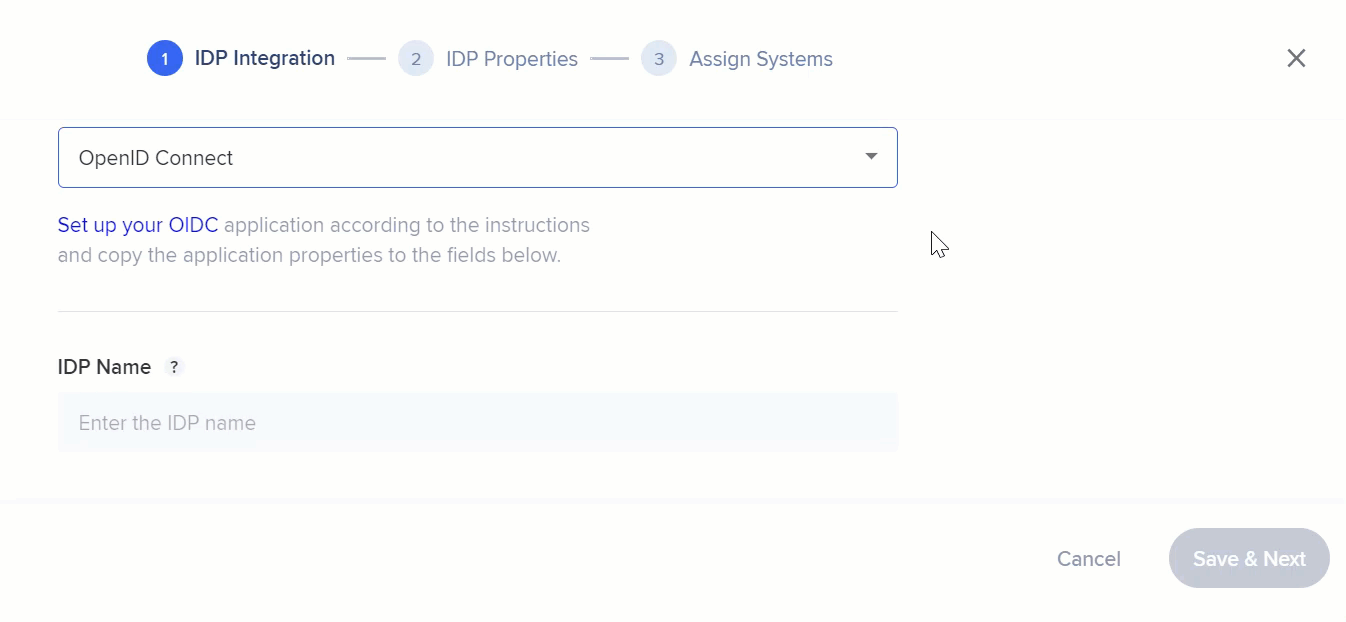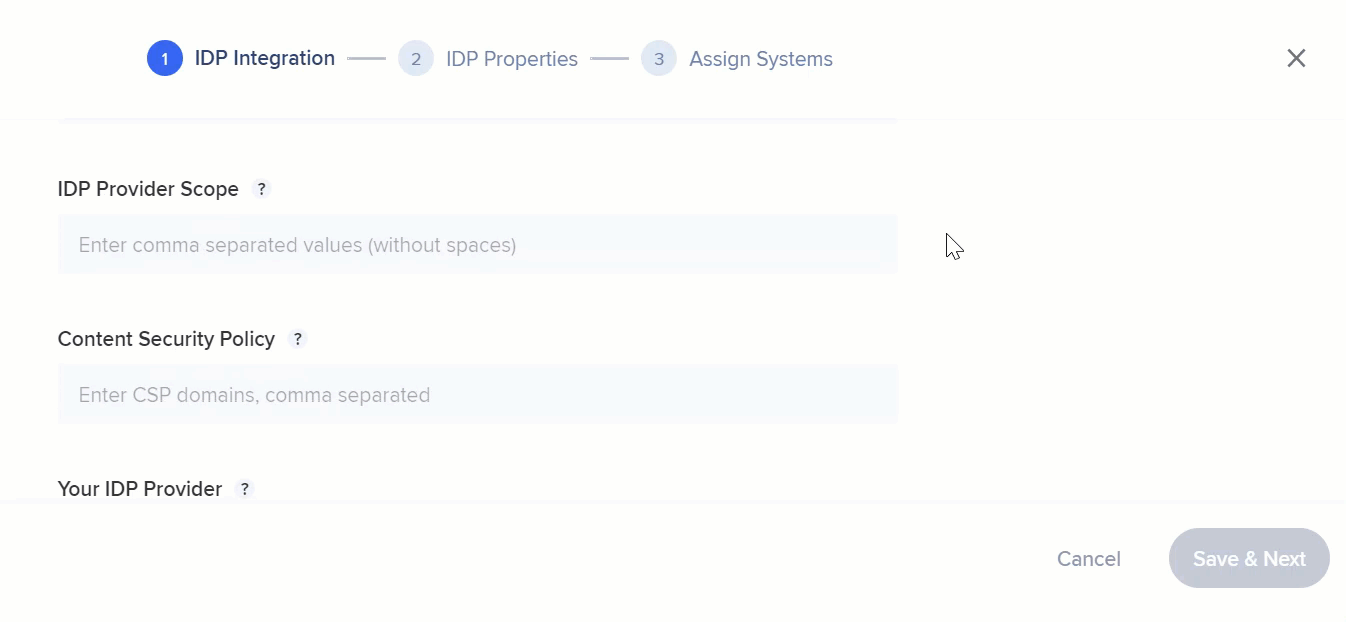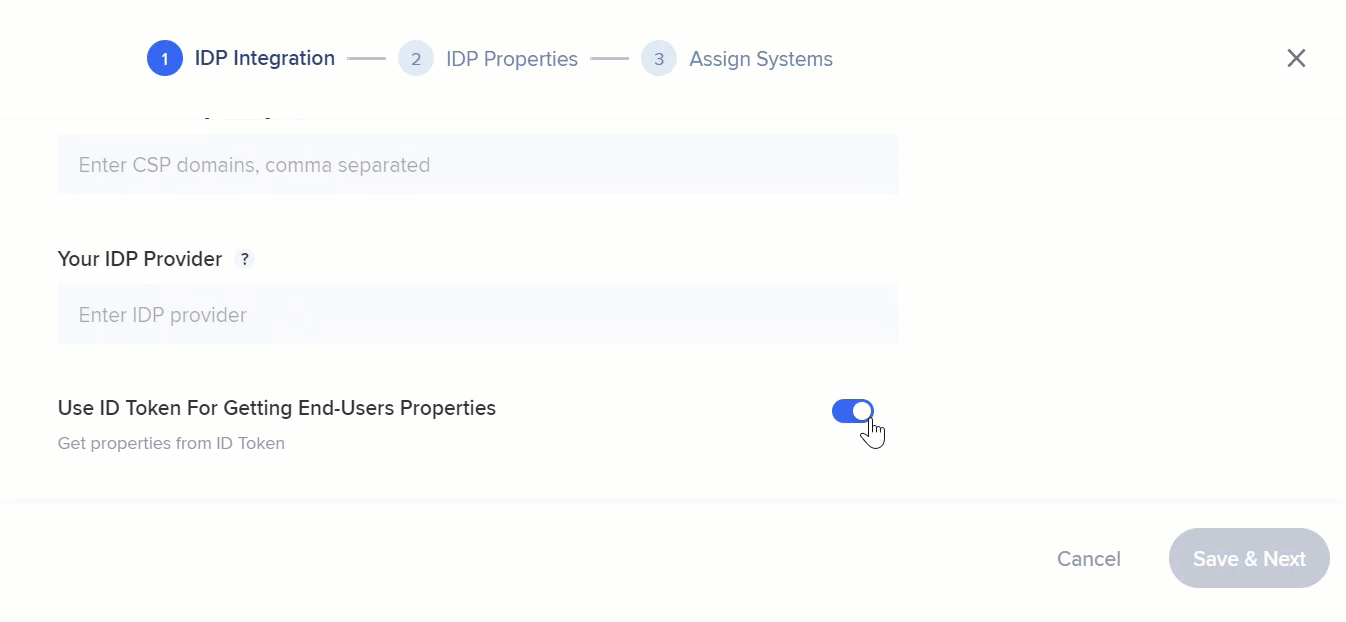
1. In the IDP Integrations page in the Admin Center, click "+ Add Identity Provider"
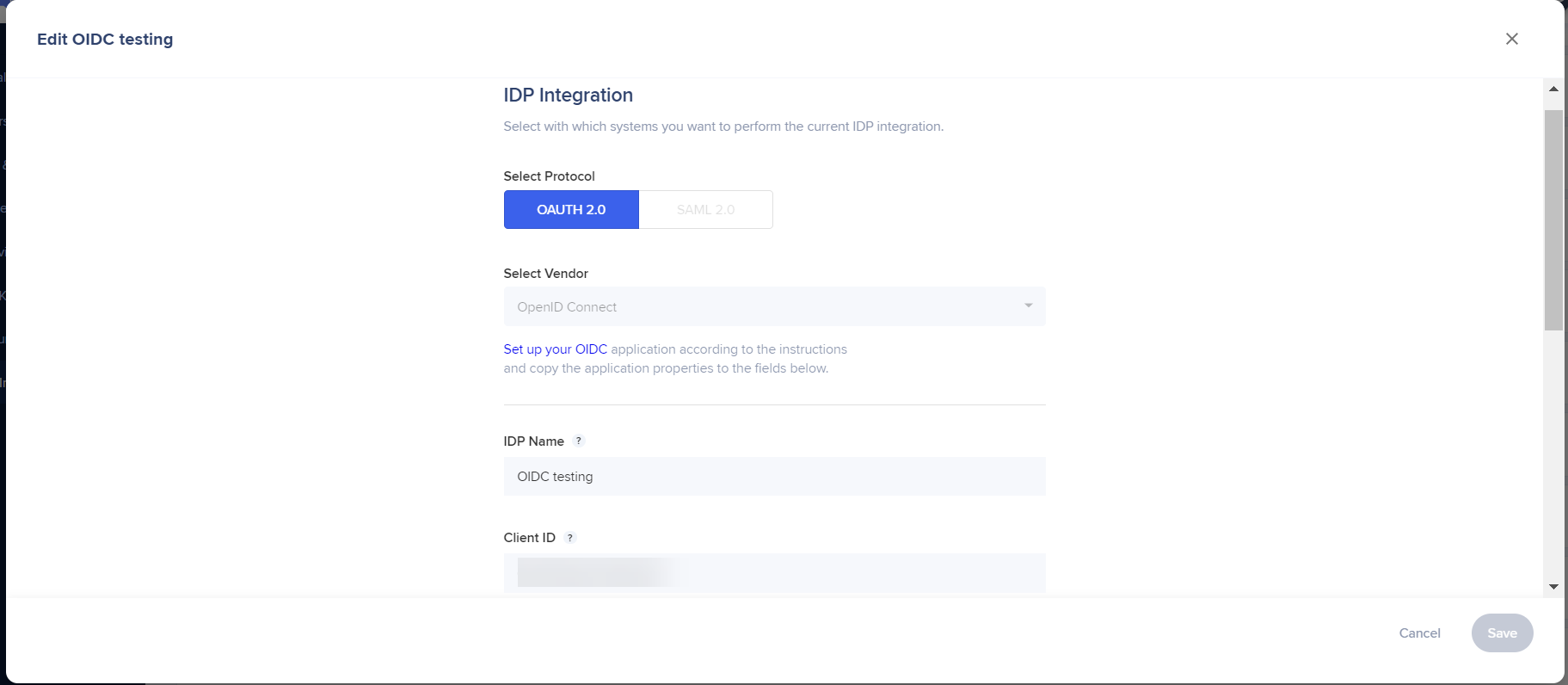
2. Select OAuth 2.0 as the protocol type
3. Provide the appropriate configuration settings for the connection
-
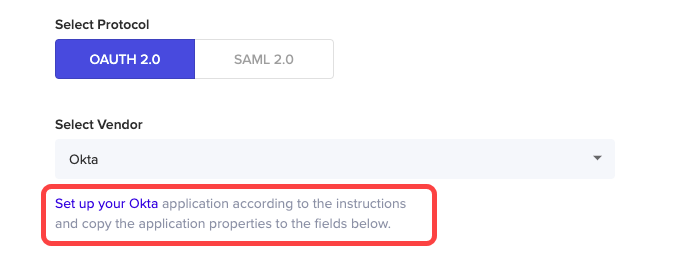
- IDP vendor: Select a vendor from the list
- IDP Name: Connection name
- Client ID: Public identifier for apps
- Client Secret: Secret known only to the application and the authorization server
- IDP Provider Domain: Domain of your organization
-
Seamless login on hidden iframe: To enable, turn on the Seamless login on hidden iframe toggle

Fields may vary pending on the IDP vendor selected.
Seamless login on hidden iframe switches the hidden login flow from using Ajax to using iframe for identity providers that require redirects.
- For OpenID Connect:
- IDP vendor: Select OpenID Connect from the Oath2.0 vendor list
- IDP Name: Connection name
- Client ID: Public identifier for apps
- Client Secret: Secret known only to the application and the authorization server
- IDP Provider Discovery URL
- IDP Provider Scope
- Content Security Policy
- Your IDP Provider
- Use ID Token For Getting End-Users Properties: Check the toggle to enable
-
4. Click "Save & Next"
A Sign Logout URL is not required.
5. Choose a unique end-user identifier to identity users by
One one identifier is required.
6. Select the desired properties and ensure the correct data type was chosen:
-
- String
- Number
- Date
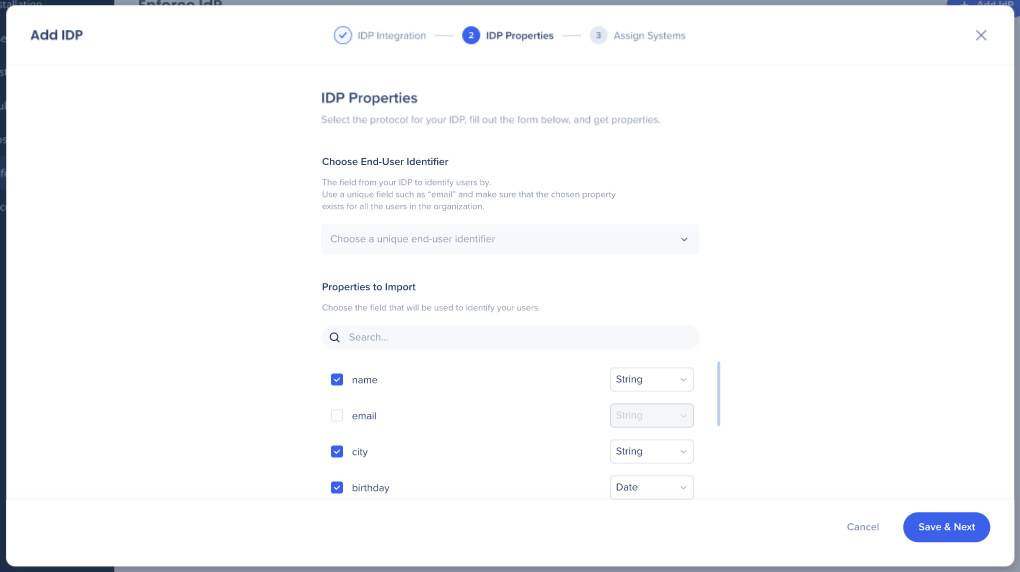
Tip
- To make sure the selected data type is suitable, you can hover above the “i” icon and check the value of that property
- If the selected data type isn't suitable for the property, a orange "!" icon will appear recommending to switch back to the identified data type
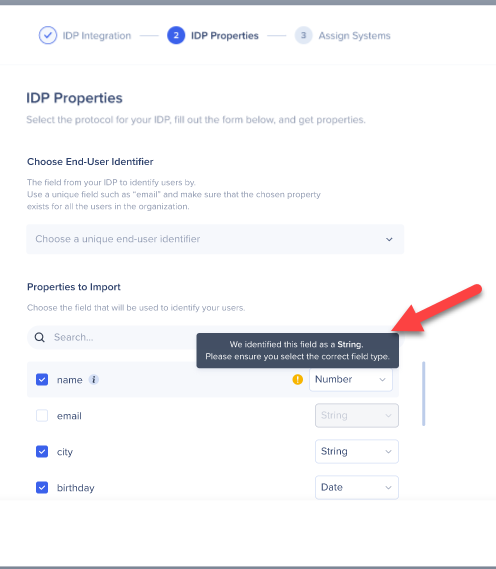
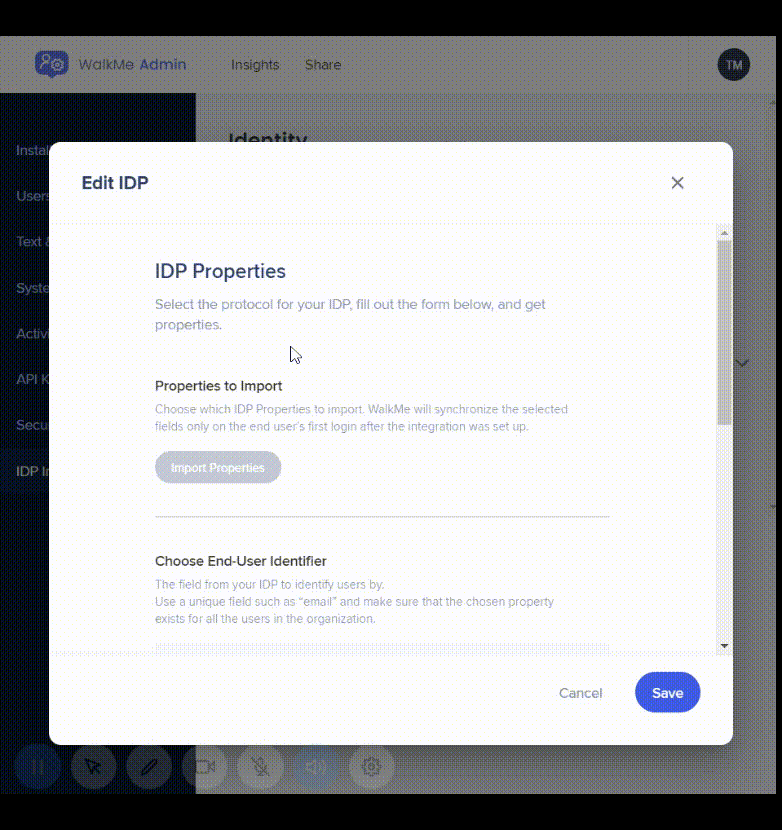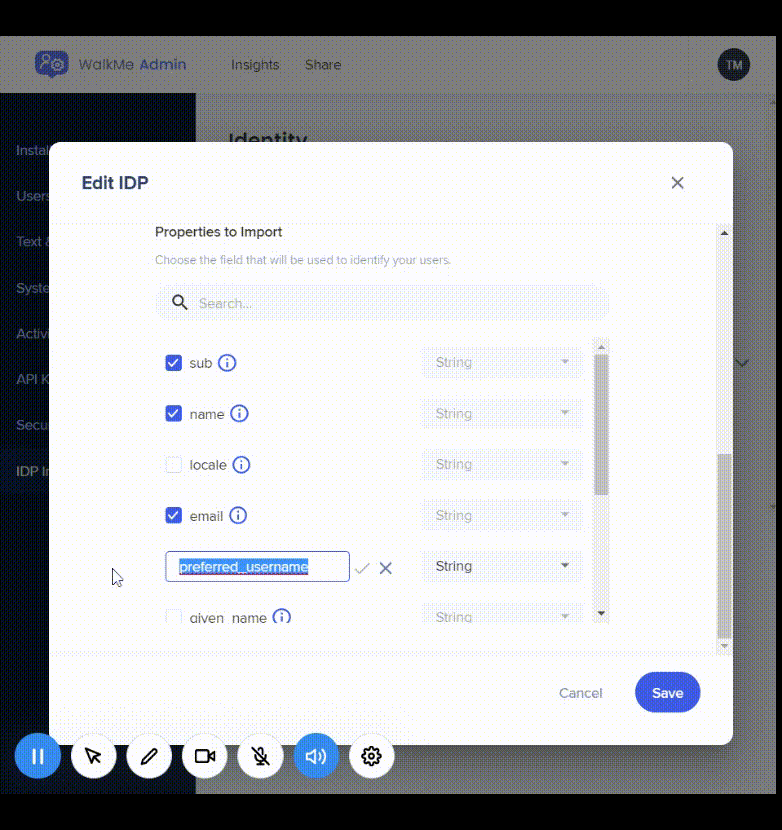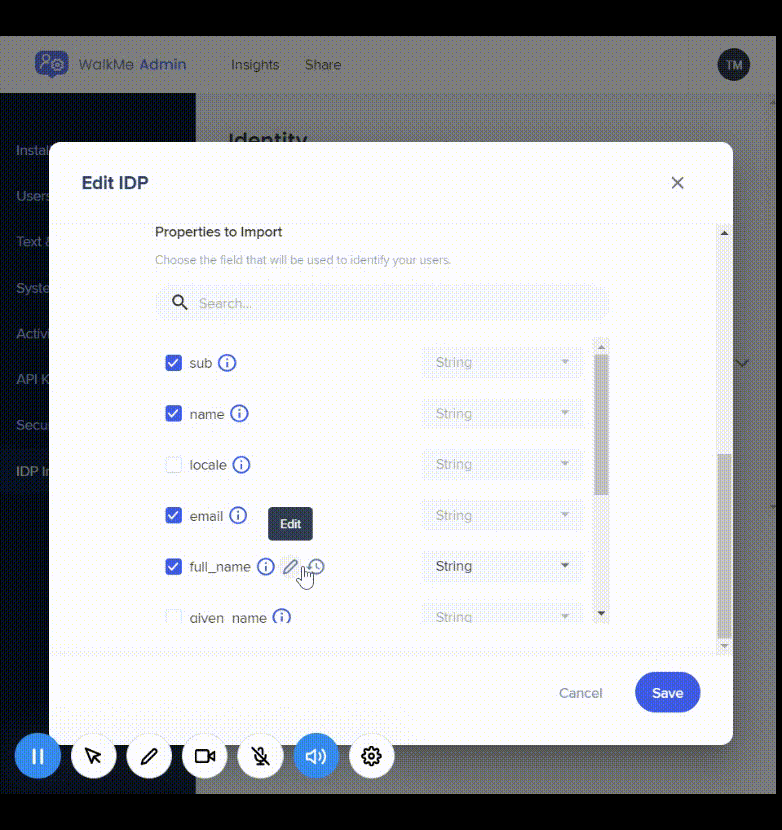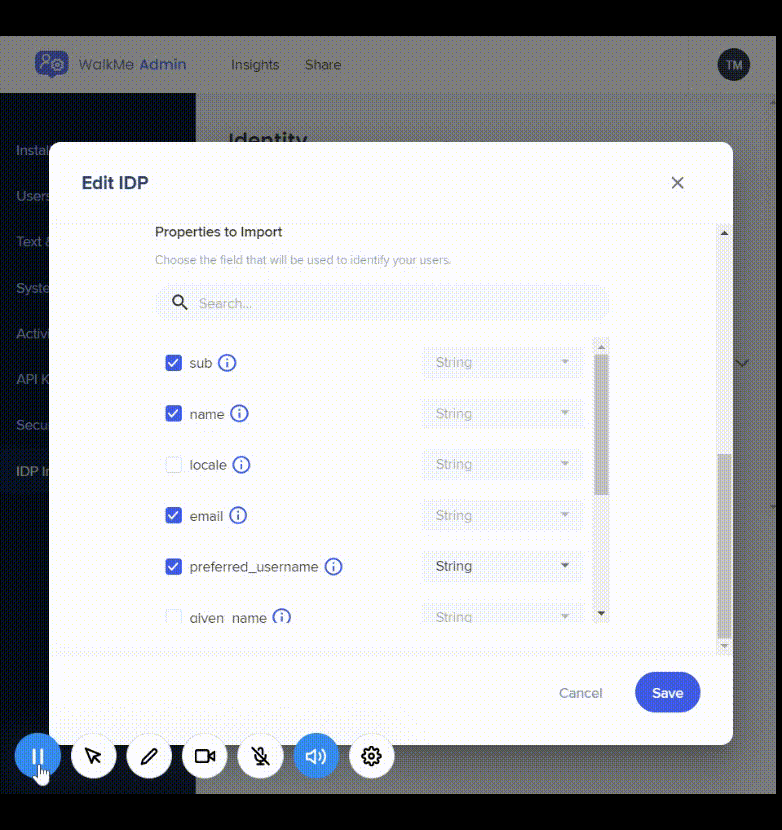
You can rename any selected property, view its original value and name, and revert back to its original value if it is overridden.
7. Select which systems you want to assign the IDP Integration to
For each system, you can separately enable IDP Integration on the desired environments.
8. Turn on or off Enforce SSO
Note
- IDP should provide the most accurate user identification, but the numbers may be not accurate when Enforce SSO is disabled
- When enforce SSO is disabled, users can use applications without authenticating to their IDP provider, and a WalkMe Id will be generated and used as user identifier
- Users can "skip" the IDP authentication by either using apps that don't require authentication at all, or by logging into the application directly via user/password, without going through the IDP login flow
9. Click "Finish"
10. A message will appear telling you whether your IDP was successfully added or not
Note
- After assigning systems, the UUID setting for the assigned systems is automatically set to IDP and settings are published so no further action is required
- The only way to change the UUID is by unassigning the system from the vendor
- You can now segment content using the imported attributes in Insights and in the Editor under User Attributes > IDP with the suitable filter conditions according to the set data field type.
Segmentation
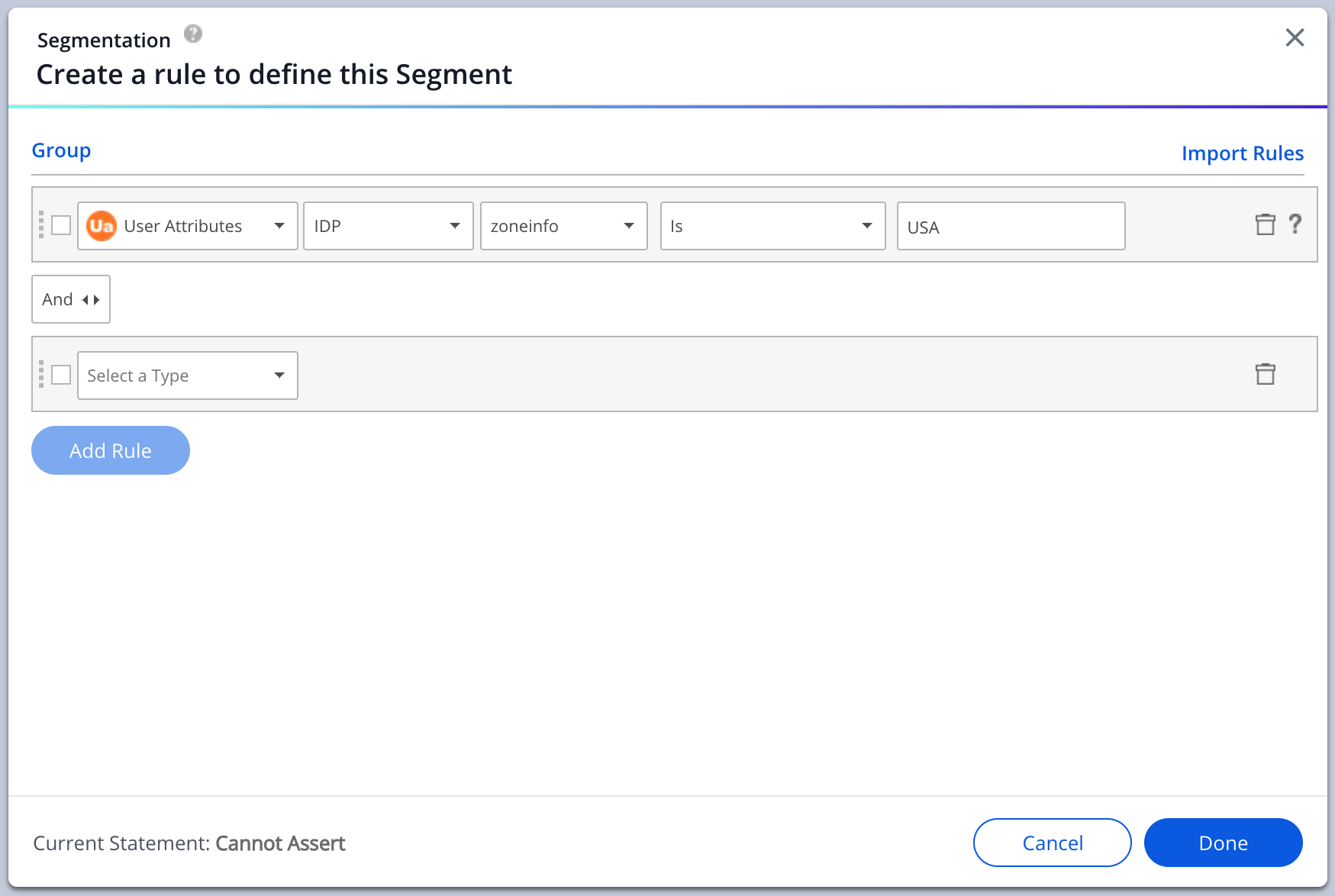
Tip
- In order to validate that users are being identified by the integration and that all the requested attributes are collected, it is recommended to view the Users page in Insights at insights.walkme.com, where all user data is displayed
- Users are added to the table only after their session has ended, so after setting up IDP it will take some time for users to be added
Insights Active Users Tab
Managing an Identity Provider
Hovering over the row of an Identity Provider will provide you with several options:
- Delete
- Manage System Assignment
- Import Properties
- Edit
- Expand

Delete
- Click on the trash icon to "delete" an identity provider
Deleting requires WalkMe Support
- It is not possible to completely delete an identity provider without contacting WalkMe Support
- Before deleting is possible, the identity provider must be unassigned to any systems using the Manage System Assignment screen
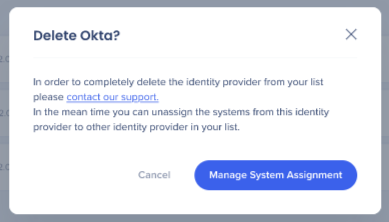
Manage System Assignment
- Click on the "+" icon to open the Manage System Assignment screen
- Select or deselect the systems you want assigned to the identity provider
- You can also use the toggle to Enforce SSO
- Click "Save Changes" once you are finished
Note
- Users cannot manage system assignment for vendors that have no imported properties - Properties will have to be imported first
- After assigning systems, the UUID setting for the assigned systems is automatically set to IDP and settings are published so no further action is required

Import Properties
- Click on the list icon and then the "Import Properties" button to edit or add additional imported properties
These attributes will be used for content segmentation and reporting in Insights.
Note
It is required to authenticate with a user that is assigned to the WalkMe app on the provider side.
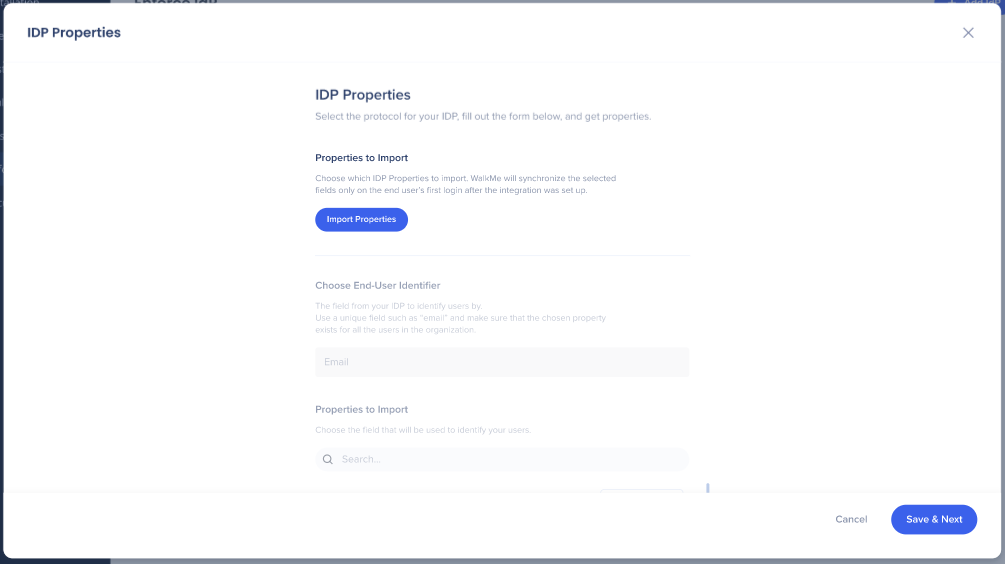
Edit
- Click on the pencil icon to edit identity provider settings
- You will be able to be able to edit all of the fields filled out in the initial identity provider configuration
Note
- Users cannot manage system assignment for vendors that have no imported properties
- Properties will have to be imported first
Expand / Collapse View
- Use the arrow icon to open and collapse the expanded view
- When expanded you will see all of the systems assigned to an identity provider and whether or not Enforce SSO has been enabled
Technical Notes
WalkMe's IDP integration supports the use of several authentication protocol including OAuth 2.0, OpenID Connect, and SAML, in order to authenticate users with their organizational IDP vendor, and to obtain user attributes that can later be used for segmentation and analytics in WalkMe. Every IDP vendor that supports these protocols should work with WalkMe. WalkMe supports SP initiated flow.
What is OAuth 2.0?
OAuth 2.0, which stands for “Open Authorization”, is a standard designed to allow a website or application to access resources hosted by other web apps on behalf of a user. OAuth 2.0 is the industry-standard protocol for authorization.
What is OpenID Connect?
OpenID Connect is a simple identity layer on top of the OAuth 2.0 protocol, which allows computing clients to verify the identity of an end-user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner.
IDP Integration currently supports the following vendors:
- Okta
- G-Suite
- ADFS
- AzureAD
- PingID
- Identity providers that use OpenID
Besides OpenID Connect, the most common authentication protocol is SAML.
SAML IDP Integration
Prerequisites
An IDP application needs to be created to serve as the "bridge" between IDP and WalkMe's Integration Center.
An instruction guide is available in the Admin Center configuration screen for all supported systems.
"Enforce SSO" Configuration
- Enabled: IDP authentication must occur before opening web pages to users, if the IDP token is not recognized then the user will be redirected to their IDP login page.
- Each time the user fails to authenticate to the IDP for reasons such as, IDP was down, invalid credentials provided, or user was not assigned to the IDP's app, SSO will be disabled for 1 hour and the User Identifier will be automatically downscaled to "WalkMe ID" method as fallback or WalkMe will not load, depending on configuration.
- After 1 hour has passed, if the IDP token is still not recognized then the user will be redirected again to their IDP login page, otherwise, login to the IDP will not be needed.
- Disabled: IDP authentication is attempted upon page load, but if there is no active token for IDP then the user won't be redirected to IDP. The User Identifier will be downscaled automatically to "WalkMe ID" method or WalkMe will not load, depending on configuration.
Limitations
Changing the User Identifier
Changing the User Identifier impacts the way WalkMe identifies end-users, as each user is being recognized as a new user, tied to their new UUID value. This could result in resetting Auto Play rules or having completed Onboarding Tasks shown as uncompleted.
- Safari browser extension is not supported
- Users should have Admin permissions for the Admin Center
- IDP must be configured on the required system
- Only one IDP Provider Domain is supported in the field
- End users should be using IDP to authenticate to that system
- If your company has CSP (Content Security Policy) it will block calls to the IDP provider
- In order to overcome this, the right URL should be added in the CSP settings of the extension configuration
- After assigning systems, the UUID setting for the assigned systems is automatically set to IDP and settings are published so no further action is required
- For the IDP changes to take effect, systems must be updated to the latest WalkMe version (this can achieved by doing a settings publish)
- For Enterprise accounts you must check "Update to the latest WalkMe version" when publishing
- Date type property supported formats:
- 2018-02-20
- 2018-02-20T14:32:00
- 12/30/2018
- String or number date types are not supported in Insights filtering and editor segmentation
- Mobile Web support:
- Mobile Web will be automatically activated after IDP setup is complete
- If Mobile Web is added after IDP / OneID has already been activated, users will need to deactivate and then reactivate IDP for Mobile Web support
Note on Two Factor Authentication (2FA)
To get the best user experience, you should not set 2FA on the WalkMe IDP for end users application. This is because the application is designed to provide a seamless and streamlined experience for users, and enabling 2FA may introduce additional steps or friction that could detract from this experience.
Solving Common Issues
User is not assigned
To prevent this from occurring, all employees need to be assigned to WalkMe. The IT person at your company should be able to assist you with this by modifying the access setting to the WalkMe app in your IDP provider to all employees.
EUID was not found in the user profile
To address this, you can either select a different EUID, which is available to all employees assigned to WalkMe, or you can individually add the missing information to the relevant users.
Expired Client / Secret Keys
If the key is expired, you will have to recreate it and then update the new keys in the relevant IDP connection in the IDP Integrations page in the WalkMe Admin Center.
Invalid Client /Secret Keys
Ensure that you have copied the correct keys and then paste them in the relevant IDP connection in the IDP Integrations page in the WalkMe Admin Center.















